Identify and Describe Tools and Techniques Used to Detect Intrusion
This is done through. Threat intelligence is frequently used to great effect in Security Information and Event Management SIEM antivirus Intrusion Detection System IDS and web proxy technologies.

Internal Scheme Of An Intrusion Detection System Download Scientific Diagram
There are two basic types of intrusion Intrusion Detection.

. It was created by Cisco and can be installed on Windows as well as a few Linux distributions. Other open source tools like Kismet OpenDLP Suricata AIDE and TRIPWIRE are also used for creating intrusion detection and prevention System. Intrusion detection encompasses tools techniques and strategies to recognize evolving threats thereby contributing to a secure and trustworthy computing framework.
Scanning processes that detect signs of harmful patterns. Snort is a well-known and currently industry-leading tool used for packet sniffing logging and intrusion detection. IDS can be a software or hardware tools.
Any exceptions are specifically noted. Typical intrusion detection systems look for known attack signatures or abnormal deviations from set norms. Free 14-day trial - no credit card required.
This chapter provides an overview of IDPS technologies. The anomaly-based intrusion detection technique defines the normal behaviors of the system such as usage frequency of commands or system calls. According to a Nilson Report the amount of global credit card fraud alone was USD 76 billion in 2010In the UK fraudulent credit card transaction losses were estimated at more than USD 1 billion in 2018To counter these kinds of financial losses a huge amount of resources are employed to identify.
Anomaly and fraud detection is a multi-billion-dollar industry. Analyzing user and attacker behavior analytics. Distinct approach to monitoring and securing data and each has distinct advantages and disadvantages.
These are also known as Knowledge-based Detection or Misuse Detection Khraisat et al 2018. It also detects on the basis of the already known malicious instruction sequence that is used by the malware. Anomaly-based misuse-based and specification-based.
It explains the key functions that IDPS technologies perform and the detection methodologies that they use. Detection Method of IDS. An IDS is either a hardware device or software application that uses known intrusion signatures to detect and analyze both inbound and outbound network traffic for abnormal activities.
There are three intrusion detection techniques. CONCLUSION Network security is primary and important of any organization. It will act as a second line of defense which may defend the network from intruders 26.
Each has a security. Intrusion is associate unwanted or malicious activity that is harmful to sensing element nodes. A comprehensive intrusion detection system IDS can understand the evasion techniques cybercriminals use to trick an intrusion prevention system into thinking there isnt an attack taking place.
IDS is either installed on your network or a client system host-based IDS. Intrusion detection is the problem of identifying unauthorized use misuse and abuse of computer systems or network resources by both system insiders and external penetrators. A typical intrusion can be the following techniques assuming that the intruder has no other information about your website than its address.
The term intrusion detection and prevention systems IDPS is used throughout the rest of this chapter to refer to both IDS and IPS technologies. Intrusion Detection System is used to monitor the malicious traffic in particular node and network. Ad Try Detectify for free and see how you can transform your web app security today.
Unlimited and automated vulnerability scans. An intrusion detection system is a monitor-only application designed to identify and report on anomalies before hackers can damage your network infrastructure. Bro has gained its reputation due to its Stateful Protocol Analysis capabilities.
Address Scans - Hackers usually scan the class C range of IP addresses around the host and reverse the DNS lookup to determine what hosts are registered to your company. Signature intrusion detection systems SIDS are based on pattern matching techniques to find a known attack. Signature-based IDS detects the attacks on the basis of the specific patterns such as number of bytes or number of 1s or number of 0s in the network traffic.
System file comparisons against malware signatures. These techniques could include fragmentation low-bandwidth attacks pattern change evasion address spoofing or proxying and more.
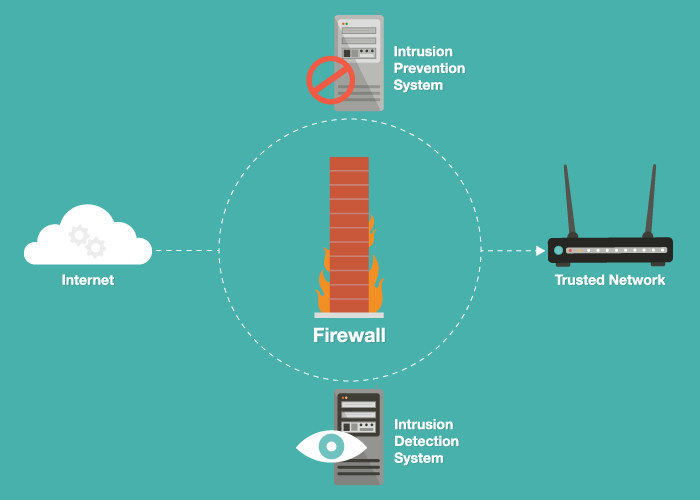
What Type Of Intrusion Detection And Prevention System Do I Need
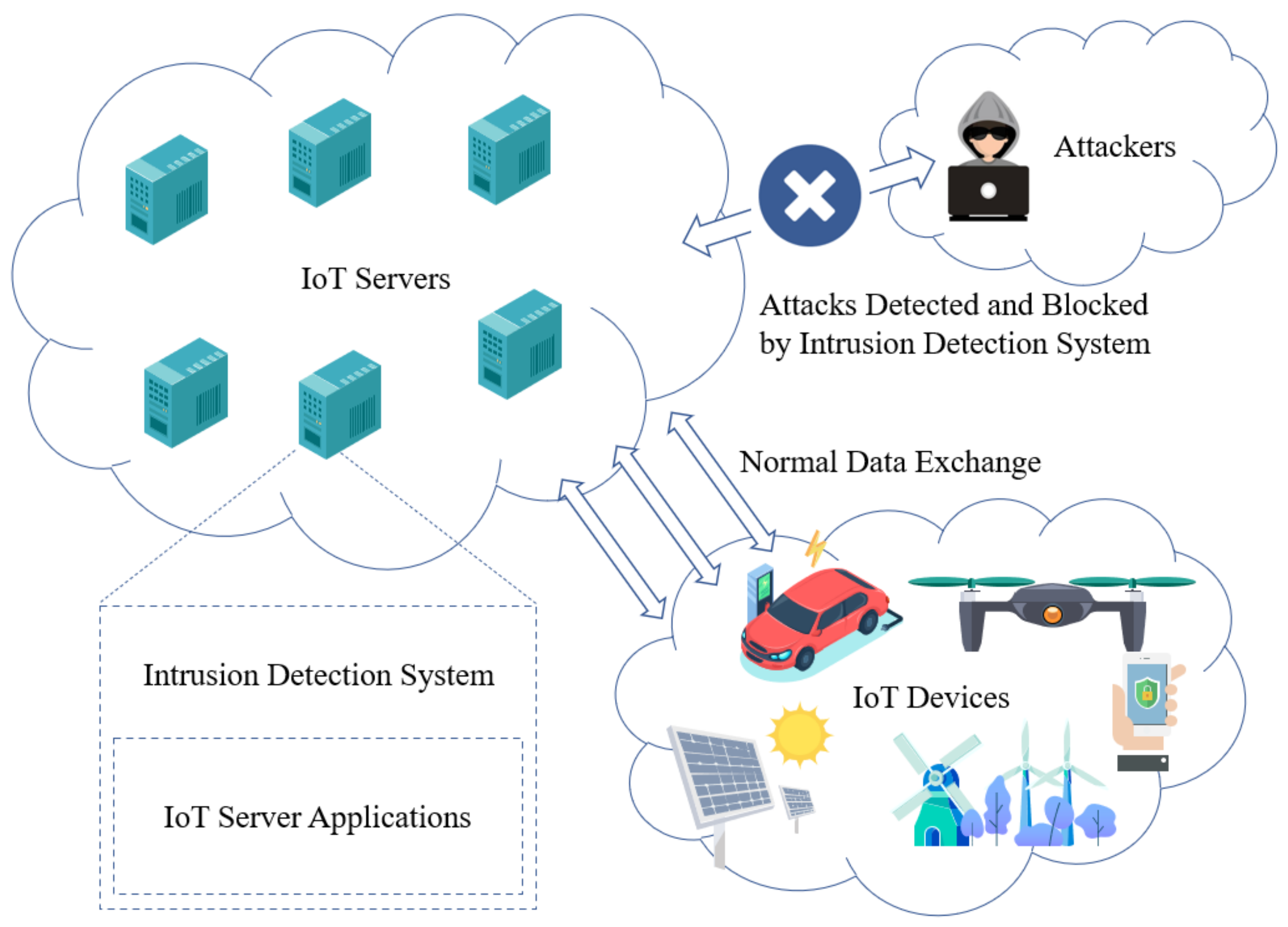
Sensors Free Full Text Sequential Model Based Intrusion Detection System For Iot Servers Using Deep Learning Methods Html
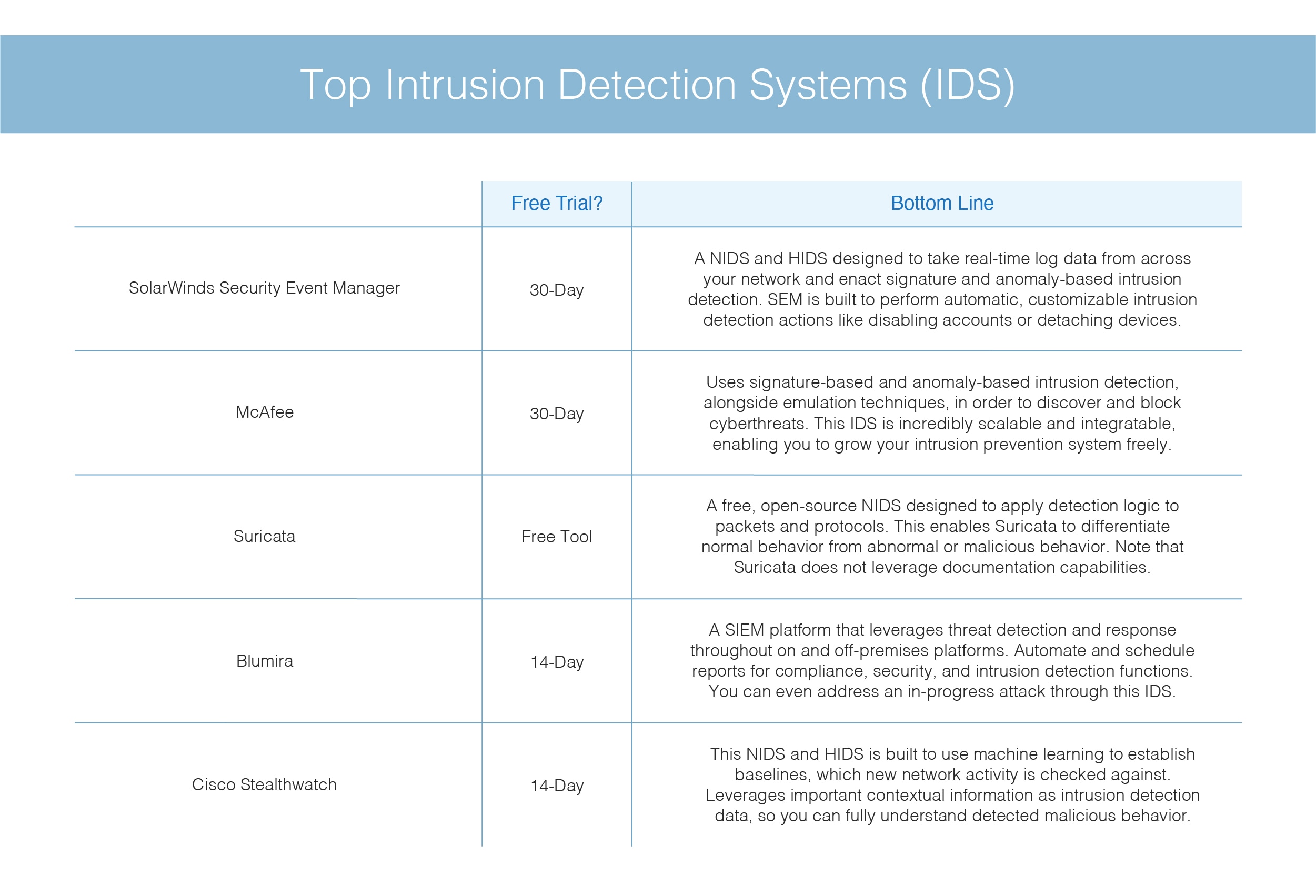
What Is An Intrusion Detection System Ids Definition And Software Solarwinds

Intrusion Detection System Architecture 37 Download Scientific Diagram
Intrusion Detection Vs Prevention Systems What S The Difference
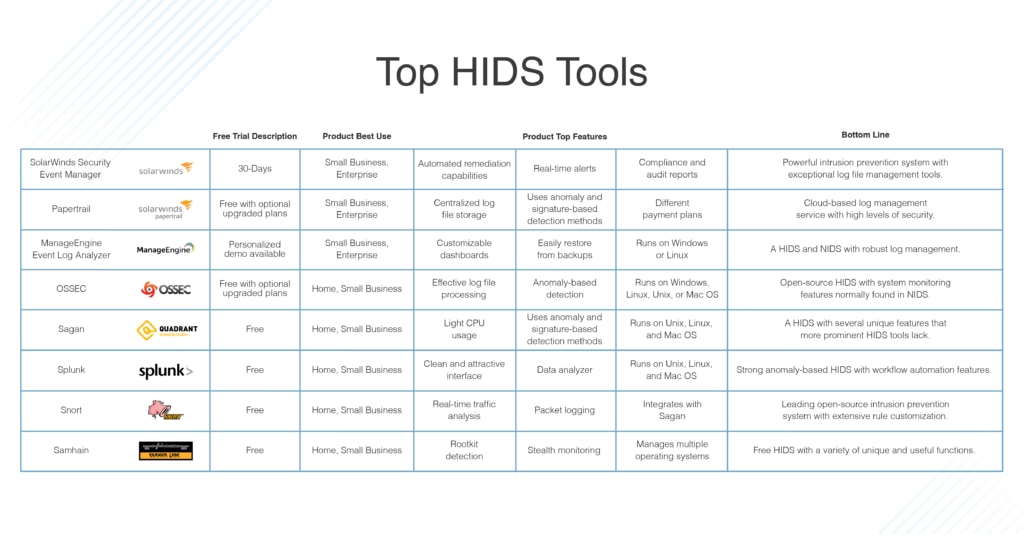
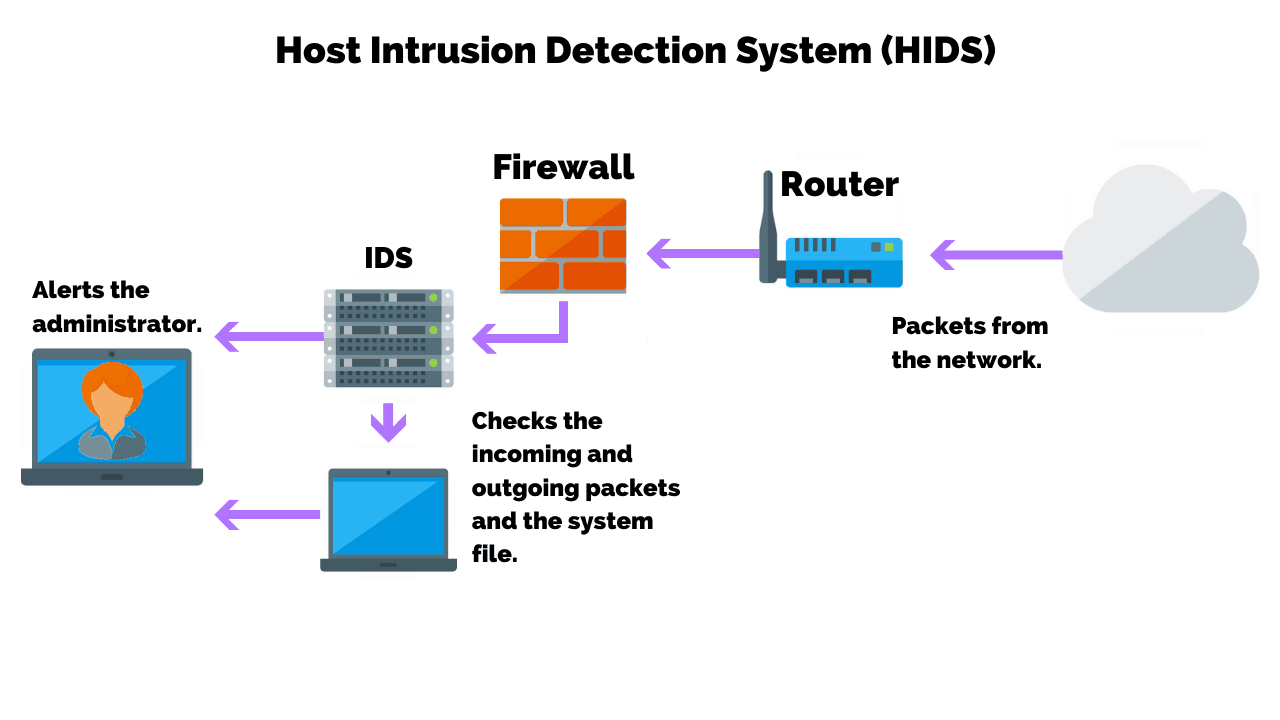
8 Best Hids Tools Host Based Intrusion Detection System Dnsstuff

Network Based Intrusion Detection System An Overview Sciencedirect Topics
Intrusion Detection Systems And Local Area Networks Download Scientific Diagram
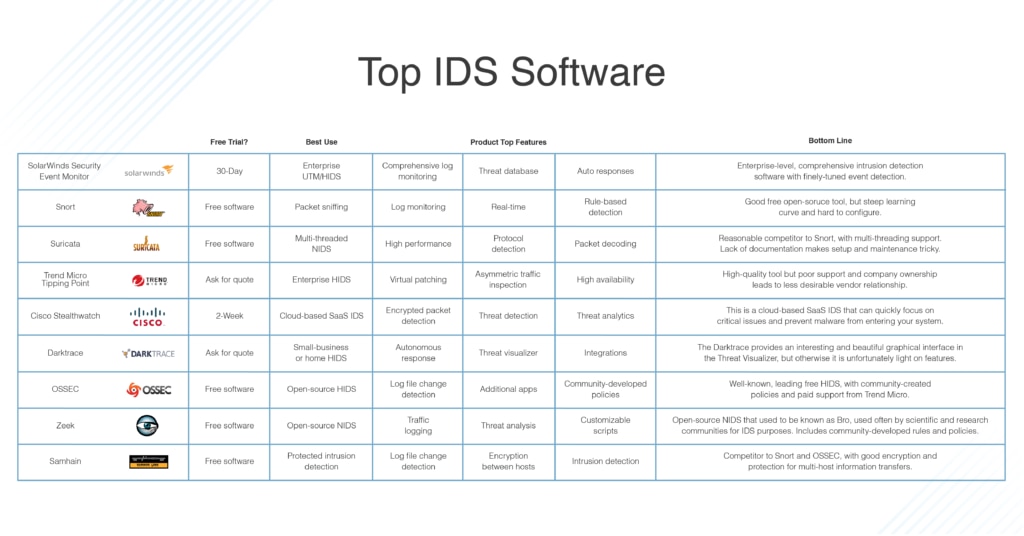
What Is An Intrusion Detection System Definition Types And Tools Dnsstuff

Best Host Based Intrusion Detection Systems Hids Tools Software
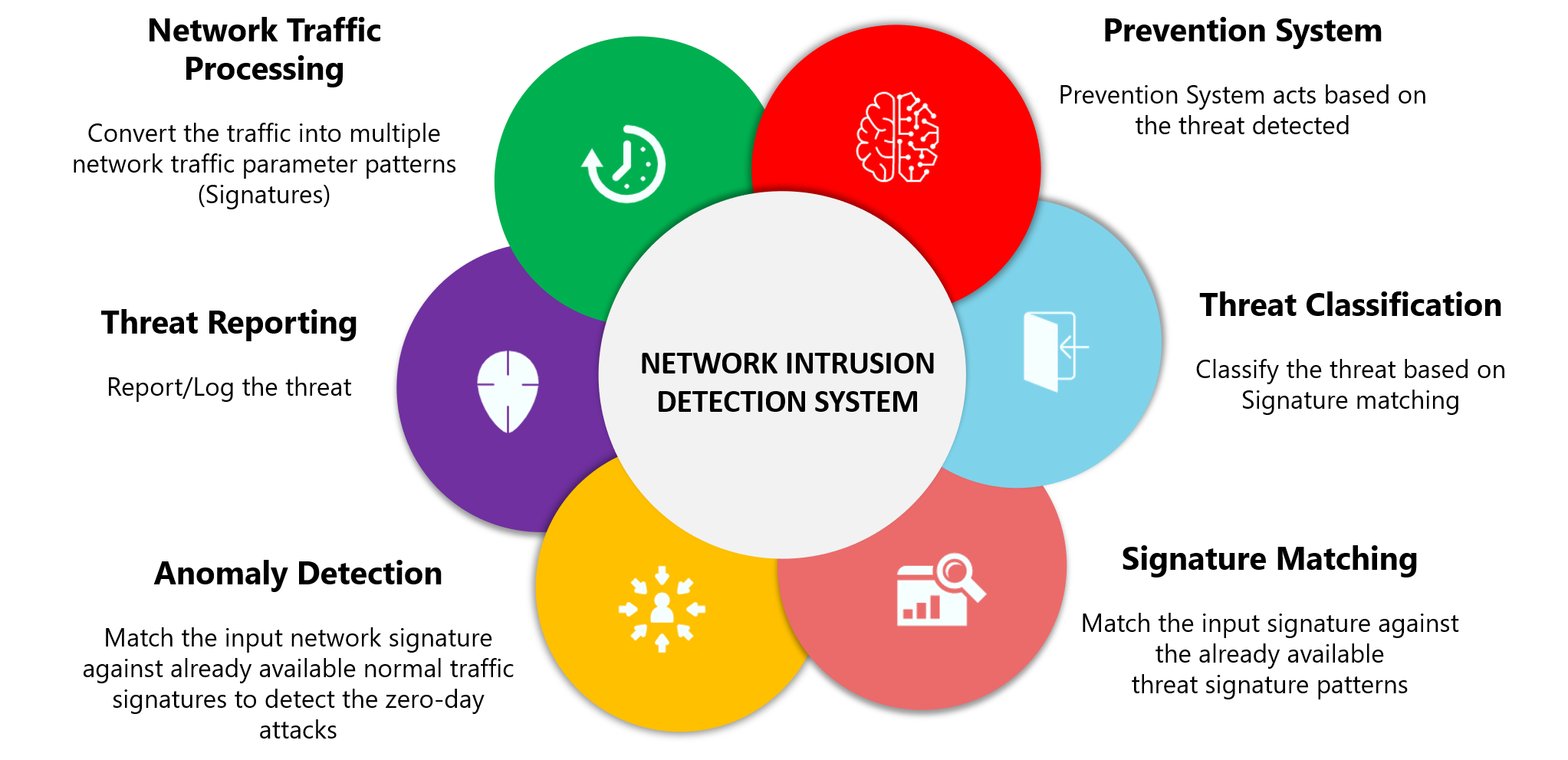
Securing The Internet Of Things With Intrusion Detection Systems Bpi The Destination For Everything Process Related

13 Best Intrusion Detection System Ids Software 2022 Paid Free
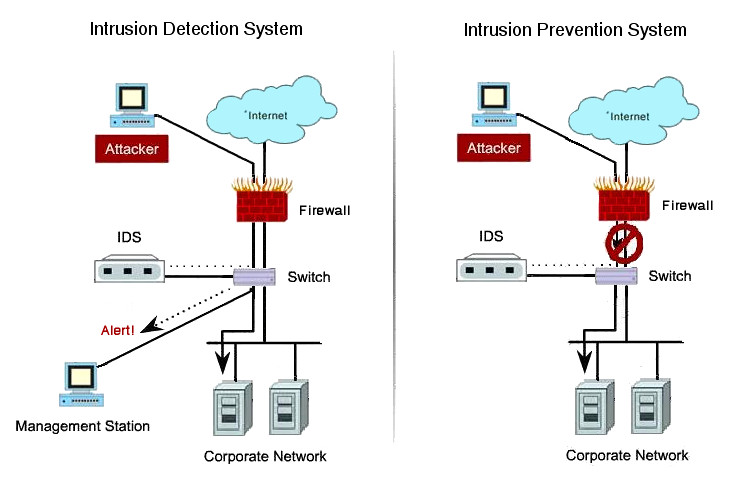
Intrusion Detection Prevention Systems The Ultimate Guide Datasilk
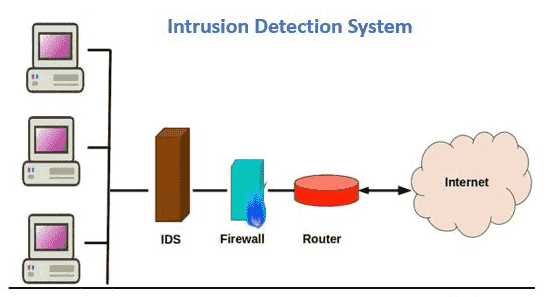
What Is An Intrusion Detection System Ids Ids Security 2022

Perform Network Intrusion Detection With Open Source Tools Azure Network Watcher Microsoft Docs
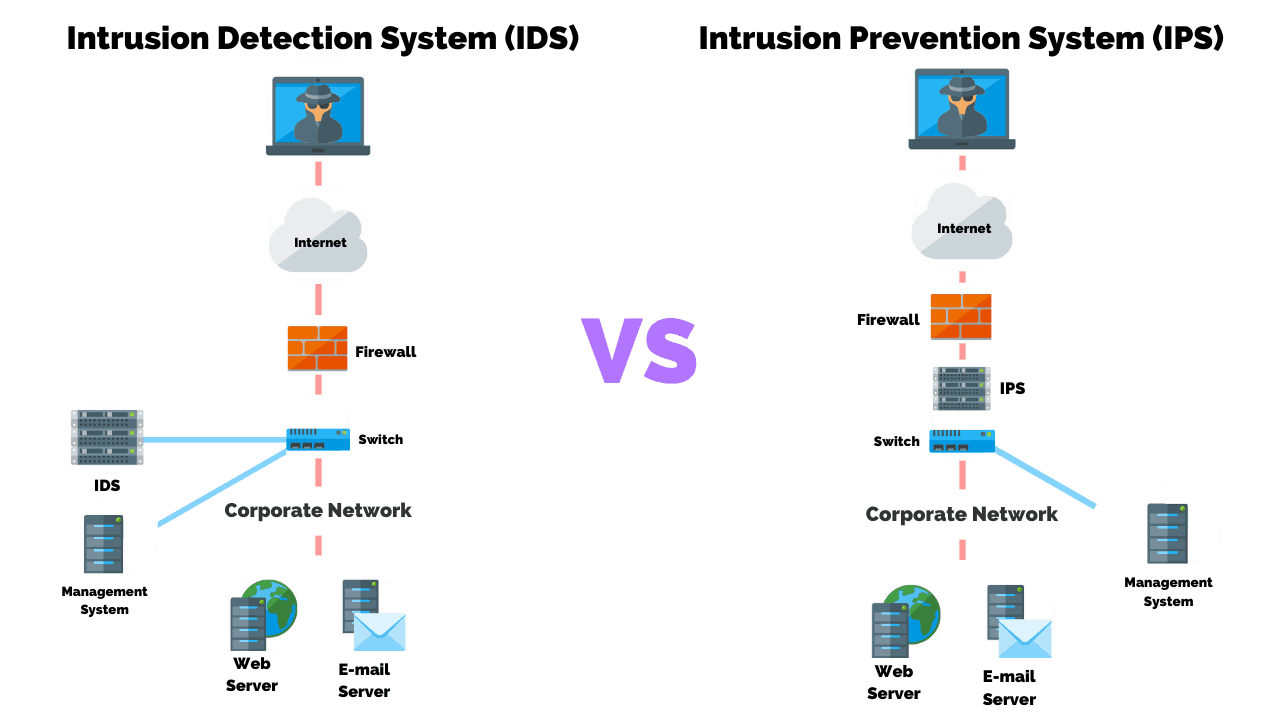
Intrusion Detection Vs Prevention Systems What S The Difference

Top 10 Best Intrusion Detection Systems Ids 2022 Rankings

Intrusion Detection And Prevention An Overview Sciencedirect Topics

Comments
Post a Comment